
With the rise of cyber threats, securing network access has become paramount. Implementing multi-factor authentication (MFA) is a crucial step towards bolstering security measures. This article delves into the intricacies of MFA and its significance in safeguarding network resources.
Let’s explore the various aspects of MFA implementation and how it fortifies network security in today’s digital landscape.
Introduction to Multi-Factor Authentication (MFA)

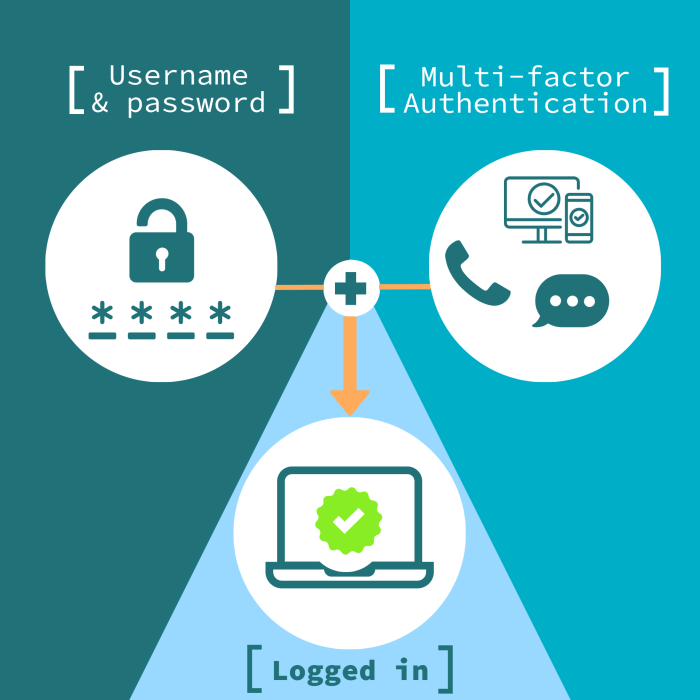
Multi-Factor Authentication (MFA) is a security process that requires users to provide two or more verification factors to gain access to a network. This added layer of security goes beyond just a username and password, making it harder for unauthorized users to breach the system.
The Importance of Implementing MFA for Network Access
Implementing MFA for network access is crucial in today’s digital landscape where cyber threats are constantly evolving. By requiring multiple factors for verification, MFA significantly enhances the security of sensitive information and reduces the risk of unauthorized access.
Factors Involved in MFA
- Something You Know:This factor typically involves information that only the user knows, such as a password, PIN, or security question. It is the most common form of authentication but is not sufficient on its own.
- Something You Have:This factor refers to a physical item that the user possesses, such as a smart card, USB token, or mobile device. This adds an extra layer of security as the user must physically have the item to authenticate.
- Something You Are:This factor involves biometric data unique to the individual, such as fingerprints, facial recognition, or iris scans. Biometric authentication is highly secure as it is difficult to replicate or steal.
Implementing MFA in Mobile App Development
Integrating Multi-Factor Authentication (MFA) into mobile applications is crucial for enhancing security measures and protecting user data. By adding an extra layer of verification beyond passwords, MFA helps in mitigating the risks of unauthorized access and data breaches.
Examples of Popular Mobile Apps Using MFA:
- Google Authenticator: Google’s own app that generates time-based one-time passwords for two-step verification.
- Microsoft Authenticator: Provides a strong authentication method by sending a notification to the user’s mobile device for verification.
- Facebook: Offers MFA through SMS codes, authentication apps, or security keys to secure user accounts.
Challenges and Considerations in Implementing MFA for Mobile App Development:
- User Experience: Balancing security with user convenience is crucial to ensure a seamless authentication process.
- Integration Complexity: Implementing MFA in mobile apps requires careful integration with existing authentication systems and user interfaces.
- Device Compatibility: Ensuring MFA methods work across various mobile devices and operating systems can be a challenge.
- Cost and Resources: Developing and maintaining MFA features can be resource-intensive, requiring ongoing support and updates.
- Security Risks: While MFA enhances security, there is a risk of vulnerabilities in the implementation process that could be exploited by attackers.
Software Development Best Practices for MFA
When it comes to incorporating Multi-Factor Authentication (MFA) into software development processes, there are several best practices that developers should follow to ensure security and a seamless user experience.
Comparing MFA Implementation Techniques
There are various techniques for implementing MFA in software development, each with its own strengths and weaknesses. Let’s compare some common approaches:
- Hardware Tokens: These physical devices generate one-time passwords for users to authenticate their identity.
- Biometric Authentication: Utilizing fingerprint, facial recognition, or iris scanning for user verification.
- Push Notifications: Sending a notification to the user’s mobile device for approval of login attempts.
- Time-based One-Time Passwords (TOTP): Generating temporary codes that expire after a short period.
Ensuring Seamless User Experience
While implementing MFA, software developers must prioritize a seamless user experience to prevent frustration and ensure adoption. Here are some ways to achieve this:
- Offer Multiple MFA Options: Allow users to choose the method that best suits their preferences and devices.
- Implement Adaptive Authentication: Use AI and machine learning to analyze user behavior and adjust authentication requirements accordingly.
- Optimize User Interfaces: Design intuitive and user-friendly interfaces for MFA prompts to guide users through the process effortlessly.
- Provide Clear Instructions: Clearly communicate the steps required for MFA setup and login to avoid confusion.
Cybersecurity Measures and MFA
In today’s digital landscape, cybersecurity is of utmost importance to protect sensitive data and prevent unauthorized access. Multi-factor authentication (MFA) plays a crucial role in strengthening cybersecurity measures for network access by adding an extra layer of security beyond just passwords.MFA requires users to provide two or more verification factors to gain access, such as something they know (password), something they have (mobile device), or something they are (biometric data).
This additional step makes it significantly harder for hackers to breach the system and access sensitive information.
Preventing Unauthorized Access and Data Breaches
- MFA helps prevent unauthorized access by ensuring that even if a hacker obtains a user’s password, they would still need the additional verification factor to gain entry.
- By adding this extra layer of security, MFA significantly reduces the risk of data breaches that can result from stolen credentials or phishing attacks.
- Unauthorized access attempts are thwarted as hackers would need more than just a password to breach the system, making it a valuable defense mechanism.
Examples of Cybersecurity Incidents Prevented by MFA
- One notable example is the Equifax data breach in 2017, where hackers exploited a vulnerability to access personal information of millions of individuals. If MFA had been implemented, the breach could have been prevented or mitigated.
- In another instance, the Twitter hack in 2020 compromised high-profile accounts to promote a cryptocurrency scam. MFA could have prevented unauthorized access to these accounts, avoiding the dissemination of fraudulent messages.
- By incorporating MFA into network access, organizations can significantly reduce the risk of cybersecurity incidents and protect sensitive data from falling into the wrong hands.
Mobile Technology and MFA
Mobile technology has revolutionized the way we access networks and services, making it more convenient and accessible than ever before. With the rise of mobile devices, the implementation of Multi-Factor Authentication (MFA) has become crucial to ensure secure network access.
Mobile Devices as MFA Factors
- Mobile devices can serve as MFA factors by utilizing biometric authentication methods such as fingerprint scanning, facial recognition, or iris scanning. These unique physical characteristics provide an additional layer of security beyond traditional passwords.
- Furthermore, mobile devices can generate One-Time Passcodes (OTPs) that are sent via SMS or through authenticator apps. These dynamic codes add an extra level of verification to ensure the identity of the user.
- Additionally, the location awareness feature of mobile devices can be leveraged for MFA. By verifying the user’s geographical location through GPS or Wi-Fi data, network access can be restricted to authorized areas only.
Future Trends of MFA with Mobile Technology
- As mobile technology continues to advance, we can expect to see more seamless and integrated MFA solutions. This may include the use of wearable devices like smartwatches or fitness trackers for MFA, providing a convenient and secure authentication method.
- Moreover, the integration of Artificial Intelligence (AI) and Machine Learning (ML) in mobile devices can enhance MFA by analyzing user behavior patterns and detecting anomalies in real-time. This proactive approach can strengthen security measures and prevent unauthorized access.
- In the future, biometric authentication methods on mobile devices may evolve to include more sophisticated techniques such as vein recognition, heart rate monitoring, or even brainwave patterns. These cutting-edge technologies will offer robust MFA solutions for enhanced network security.
Technology & Software Solutions for MFA
In the realm of network security, implementing multi-factor authentication (MFA) is crucial to safeguard sensitive data and prevent unauthorized access. Various technological solutions and software tools are available to facilitate the seamless integration of MFA into network access systems.
Biometric Authentication
Biometric authentication is a cutting-edge technology that leverages unique biological traits such as fingerprints, facial recognition, or iris scans to verify user identity. By incorporating biometric authentication as one of the factors in MFA, organizations can enhance security measures and reduce the risk of identity theft or unauthorized access.
Hardware Tokens
Hardware tokens are physical devices that generate one-time passwords (OTPs) or cryptographic keys to authenticate user identity. These tokens add an extra layer of security to the MFA process, ensuring that only authorized individuals can access the network. Hardware tokens are ideal for environments where mobile devices may not be suitable for MFA implementation.
Smart Cards
Smart cards are another popular technology for MFA implementation, especially in enterprise settings. These cards contain embedded microchips that store user credentials and require a PIN or biometric scan for authentication. Smart cards offer a secure and convenient way to verify user identity and are compatible with a wide range of access control systems.
Identity and Access Management (IAM) Platforms
IAM platforms provide centralized control and management of user identities, permissions, and access rights. By integrating MFA capabilities into IAM solutions, organizations can enforce strict security policies and ensure compliance with industry regulations. IAM platforms offer scalability and flexibility, making them an essential component of a comprehensive MFA strategy.
Cloud-Based MFA Solutions
Cloud-based MFA solutions offer a cost-effective and scalable approach to implementing MFA across multiple devices and applications. These solutions leverage cloud infrastructure to deliver secure authentication services without the need for extensive on-premises hardware or software installations. Cloud-based MFA solutions are ideal for organizations looking to streamline the deployment of MFA across their network infrastructure.
Web Development Practices for MFA
Integrating Multi-Factor Authentication (MFA) into web development projects is crucial for enhancing security and ensuring secure user authentication. By implementing MFA, web developers can add an extra layer of protection to prevent unauthorized access to user accounts and sensitive information.
Tips for Optimizing MFA Implementation in Web Development Projects
- Choose the Right MFA Methods: Select MFA methods that align with the security needs of your website and the preferences of your users. Options may include SMS codes, email verification, biometric authentication, or hardware tokens.
- Implement Strong Password Policies: Encourage users to create strong and unique passwords to complement the MFA process. This reduces the likelihood of successful brute force attacks.
- Regularly Update MFA Protocols: Stay updated with the latest security standards and technologies to ensure that your MFA implementation remains effective against evolving threats.
- Provide Clear Instructions: Clearly communicate the MFA process to users, guiding them through the setup and authentication steps to avoid confusion and frustration.
User Interface Considerations for Designing MFA Workflows for Web Applications
- Simple and Intuitive Design: Create user-friendly interfaces that make the MFA process easy to understand and navigate, reducing the risk of user errors.
- Responsive Design: Ensure that MFA workflows are optimized for various devices and screen sizes to provide a seamless authentication experience across platforms.
- Visual Feedback: Use visual cues such as progress indicators, success messages, and error alerts to keep users informed about the status of their authentication process.
- Accessibility Features: Implement accessibility features to accommodate users with disabilities, making MFA workflows inclusive and easy to use for all individuals.
Networking Protocols and MFA
When it comes to enhancing networking protocols with Multi-Factor Authentication (MFA), the focus lies on ensuring secure network access while maintaining optimal performance. Let’s delve into how MFA can be integrated into various networking infrastructures to bolster cybersecurity measures.
Impact on Network Performance and Latency
- Implementing MFA in networking protocols can introduce an additional layer of security, which may lead to a slight increase in authentication time.
- However, advancements in MFA technologies have minimized the impact on network performance, ensuring that the authentication process remains efficient.
- Organizations should weigh the benefits of heightened security against potential minimal latency issues to determine the best approach for their network.
Compatibility with Different Network Infrastructures
- Virtual Private Networks (VPNs) can seamlessly integrate MFA to authenticate users before granting access to the network, adding an extra level of protection.
- Cloud networks can also benefit from MFA by ensuring that only authorized users can access sensitive data and applications stored in the cloud.
- It is essential for organizations to assess the compatibility of MFA solutions with their specific network infrastructure to maximize security without compromising functionality.
Gaming Hardware and MFA
When it comes to implementing Multi-Factor Authentication (MFA) for user authentication, gaming hardware can play a significant role in enhancing security measures. Gaming peripherals offer unique opportunities for incorporating additional authentication factors, thereby strengthening the overall security of systems.
Utilizing Gaming Peripherals for MFA Factors
- Gaming peripherals such as gaming mice, keyboards, and controllers can be utilized as MFA factors by leveraging their unique features and functionalities. For example, the precise movements of a gaming mouse or the combination of buttons pressed on a gaming keyboard can serve as secondary authentication factors.
- By integrating gaming peripherals as MFA factors, users can benefit from a more personalized and interactive authentication process. This not only enhances security but also provides a seamless and user-friendly experience.
Challenges and Benefits of Integrating MFA with Gaming Hardware Devices
- Challenges:One of the challenges of integrating MFA with gaming hardware devices is the need for compatibility and customization. Not all gaming peripherals may support MFA integration, requiring additional development efforts to ensure seamless functionality.
- Benefits:On the other hand, the benefits of integrating MFA with gaming hardware devices are numerous. These devices offer unique input methods and sensor capabilities that can enhance the security of authentication processes. Moreover, leveraging gaming peripherals for MFA adds an extra layer of protection without compromising user experience.
Smart Technology Integration with MFA
Integrating multi-factor authentication (MFA) with smart technologies like IoT devices is crucial in enhancing security measures and protecting user data. By implementing MFA, users can have an added layer of protection when accessing their smart devices and ensuring that only authorized individuals can control these devices.
Benefits of MFA for Smart Technology
- MFA adds an extra layer of security to prevent unauthorized access to smart devices, reducing the risk of data breaches or cyber attacks.
- Enhanced user authentication through MFA helps in safeguarding personal information and sensitive data stored on IoT devices.
- By requiring multiple factors for authentication, MFA can significantly increase the overall security posture of smart home devices.
Security Implications of MFA Integration
- Integrating MFA with smart home devices can mitigate the risks of unauthorized access by malicious actors, ensuring that only authenticated users can control these devices.
- Securing IoT devices with MFA can prevent potential vulnerabilities and protect against cyber threats that target interconnected smart technologies.
- Implementing MFA in smart technology applications can create a more secure environment for users by verifying their identity through multiple authentication factors.
Examples of MFA in Smart Technology Applications
- Smart door locks that require biometric authentication along with a password or PIN for access.
- Voice-controlled assistants that utilize facial recognition and a unique passphrase for user verification.
- Smart thermostats that implement MFA through fingerprint scanning and a one-time passcode sent to the user’s mobile device.
Final Thoughts
In conclusion, the adoption of multi-factor authentication for network access is indispensable in mitigating cybersecurity risks. By incorporating MFA, organizations can enhance their defense mechanisms and thwart potential breaches effectively. Stay vigilant and prioritize security to safeguard your network infrastructure.
FAQ Summary
How does MFA enhance network security?
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before granting access, reducing the risk of unauthorized entry.
What are the common challenges in implementing MFA?
Some challenges include user resistance to change, compatibility issues with existing systems, and the need for robust user training to ensure smooth implementation.
Can MFA prevent all types of cyber threats?
While MFA significantly reduces the risk of unauthorized access, it cannot completely eliminate all cyber threats. It is essential to combine MFA with other security measures for comprehensive protection.





